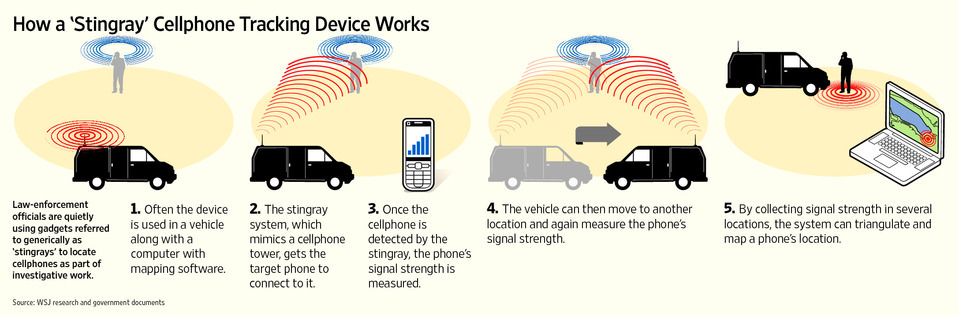
How stingray works
Credit: WSJ
StingRay (the brand name) & stingray (generic) devices can trace your mobile (cell) phone by effectively doing a, “man in the middle”, attack on it. Perhaps most surprising is evidence that versions of this technology have been available for over 10 years.
http://www.tomsguide.com/us/cellphone-tracker-stingray,news-21718.html
http://www.extremetech.com/mobile/184597-stingray-the-fake-cell-phone-tower-cops-and-providers-use-to-track-your-every-move
http://www.wired.com/2015/09/feds-need-warrant-spy-stingrays-now/
http://www.wired.com/2015/03/feds-admit-stingrays-can-disrupt-cell-service-bystanders/ / covered his tracks Daniel Rigmaiden arrested FBI filing tax returns dead people collecting refunds authorities FBI foolproof system avoid detection always anonymous Internet used fake IDs prepaid debit cards loopholes exposed cellular broadband modem AirCard his computer connect Internet court access documents pretrial research strangenew investigative techniques cellphone mobile towers device called Stingray U.S. government secretly using Stingray military use law enforcement locate track suspects cellular connections first civilians technology case public knowledge more information about Stingrays IMSI catchers cell-site simulators fake cell towers use devices law enforcement routinely obscured in court records major manufacturer requires police departments never disclose they use devices Department of Justice DOJ agencies FBI U.S. Marshals Service Drug Enforcement Administration DEA Bureau of Alcohol Tobacco Firearms and Explosives ATF routine cases warrant before using Stingray agencies destroy data collected non-suspects targeted suspect located pleaded guilty several counts tax fraud sentenced time served court probation research electronic surveillance consultant Stingray technology use Stingrays commonplace United States all levels of law enforcement widespread surveillance tool never heard Stingray mounted car van law-enforcement agencies intercept your cellphone cell phone mobile phone signal middleman between you nearest cell tower protocols built into cellular networks your phone's location determined telephone calls logged target device located allow text messages phone calls deciphered StingRay brand name Harris Corp. Melbourne Florida IMSI catchers Stingrays 10 years ago StingRay device complete target tracking location solution low-power system designed for vehicular operations The American Civil Liberties UnionACLU FBI DEA Secret Service National Security AgencyNSA U.S. Marshals Service Immigration and Customs Enforcement ICE ATF U.S. Army Navy Marine Corps use Stingrays law-enforcement cases IMSI catchers federal agencies technology 9/11 Department of Homeland Security DHS funding programs cost $150,000 affordable state local police forces force DOJ's new law-enforcement agencies federal departments deputy U.S. attorney general DHS Border Patrol Secret Service agency DOJ rules military intelligence agencies NSA CIA state local law-enforcement agencies use Stingrays federal government constitutional use of the devices recent cases U.S. Supreme Court ruled cellphone-tracking methods violated Fourth Amendment warrant Stingray impersonates cellular tower cellphones try connect forward incoming outgoing calls texts legitimate cell tower mobile phone cell phone cellphone users tries to connect cell tower identifies itself track suspect's cellphone any cellular-enabled device within range cellphone signal Stingray's signal find devices vehicles buildings Stingray forces all cellphones range connect broadcasting signal stronger signal transmitted real cell towers telling cellphones signal strongest connected Stingray requests phone identifying serial number serial numbers law-enforcement International Mobile Subscriber Identity IMSI SIM card cell tower electronic serial number ESN mobile equipment identifier MEID device identifier IMSI numbers phones mobile cellular-service providers investigators Stingrays collect IMSI numbers target device located serial numbers suspect's cellphone interrogation send signals response geolocation techniques measuring angle direction signal strength distance signal time of flight distance targeted device identification data innocent civilians' information phones identify themselves leaked documents IMSI catchers IMSI catcher 3G 4G connections unavailable phones downgrade to 2G Hailstorm intercept 4G connections forced downgrade capabilities U.S. cellular carriers Airplane Mode app SnoopSnitch detect Stingray activity Android devices Qualcomm chipsets apps CEO ESD America Cryptophone encrypts detects Stingrays phone's baseband radio stack CryptoPhone remotely control phone malware spyware under attack warning within half a mile IMSI catcher switch SIM cards read phone's International Mobile Station Equipment Identity IMEI number IMEI IMSI SIM cards broadcast ESN MEID search warrant tracking devices shut off users maintain anonymity /